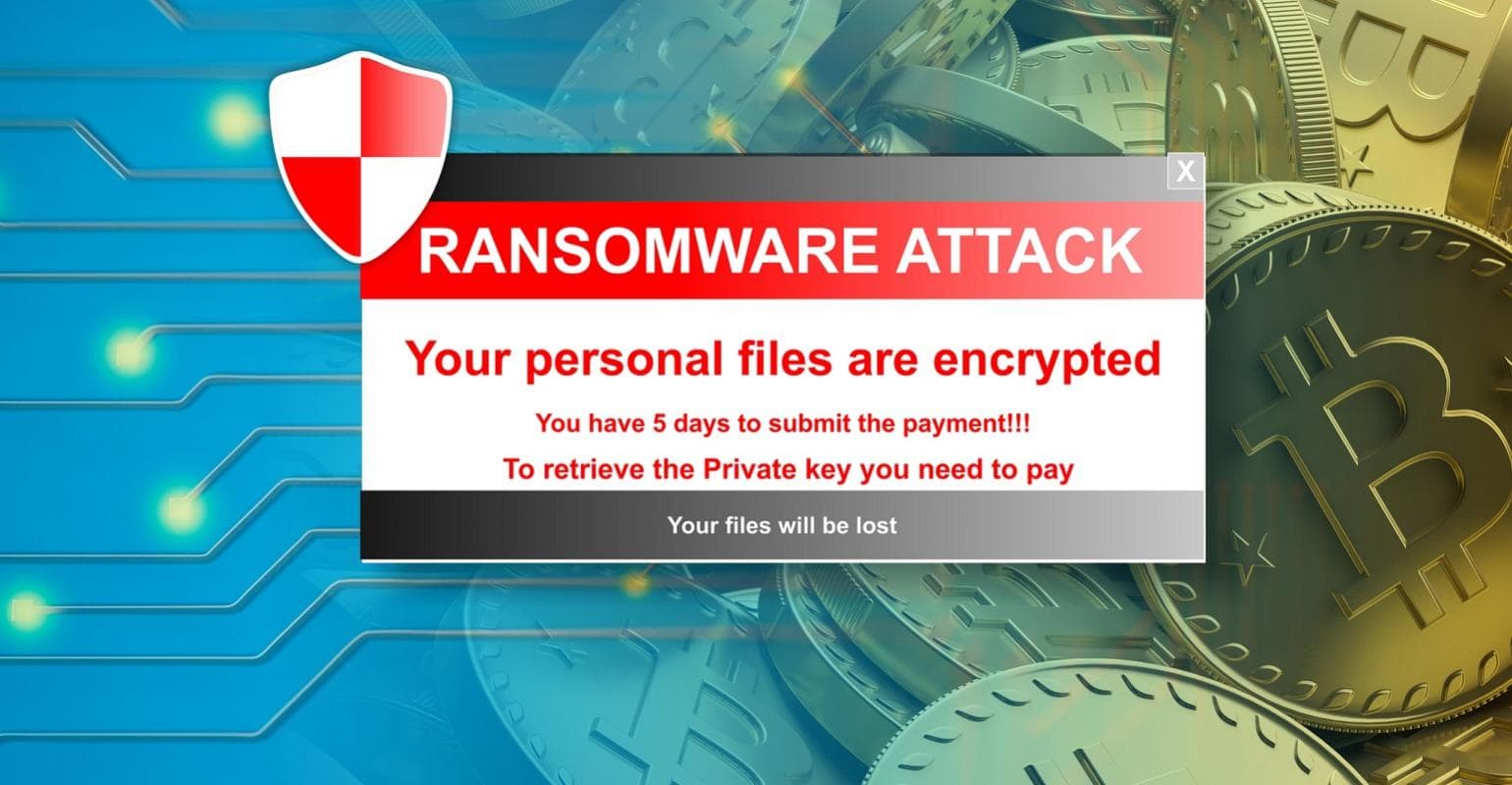
Ransomware attacks that have been effective in the past year have raised awareness about internet security around the globe. Data breaches are on the rise as a result of ransomware attacks, which put firms without adequate security measures in danger. Getting your data back after a ransomware assault is getting more and more expensive because of more complex attacks. Cybersecurity Ventures estimates that ransomware expenditures would exceed $265 billion by the year 2031, according to their research.
From assaults on big healthcare institutions to technological enterprises, no industry is safe from ransomware attacks, and corporations need to establish effective protection measures to avoid their security teams feeling attack fatigue.
Organizations are depending on a Zero Trust architecture to safeguard both on-premises and cloud assets in order to avoid such assaults. Zero Trust guarantees applicable least privilege and safe access to company resources, lowering the attack surface and decreasing the risks of ransomware assaults. By managing all aspects of network security with a Zero Trust solution, IT administrators may drastically decrease the risks of cyber attacks across their companies.
It is possible for information technology (IT) administrators to limit the resources that each individual employee has access to by using zero trust. In order to lessen the impact of ransomware assaults, this is an absolute necessity. Even in the event of a vulnerability, hackers are restricted to only a few resources available to the single user they compromised because of Zero Trust.
The Mysteries of Ransomware
Creating Entry Barriers with Zero Trust
Here’s how Zero Trust enhances overall security posture:
Segmentation of the Network
This allows enterprises to set internal trust boundaries for granular management of traffic flow, enabling secure network access and deploy network monitoring. By enabling only specified members to access certain programs and resources, the attack surface is considerably minimised, offering a distributed security solution.
Trust Zones
IT administrators can set up “Trust Zones” to restrict access to firm resources for certain groups of users. As a result, the number of possible routes for malevolent attackers to get access to critical resources is reduced to a minimum.
Management of the Infrastructure
An key aspect of a Zero Trust strategy is the capacity to efficiently monitor networks through centralized administration. This permits data to be analyzed by analytic tools and technologies that may increase network visibility, discover new risks, or assist compliance reporting.
Looking Ahead
To keep up with the ever-evolving ways of hackers, the cybersecurity industry is constantly innovating new technology to provide businesses with the tools they need to combat security threats.
The Zero Trust model is an example of a security system that can keep businesses safe from internet threats. By adopting authentication and segmentation rules, creating Trust Zones and carefully monitoring all network activity, firms can arm themselves with the necessary weapons against ransomware and other attacks.
Want to learn more about preventing ransomware attacks in your company? Check out our Essential Guide to Preventing Ransomware Attacks and discover how organizations all over are benefiting from Zero Trust Network Access (ZTNA) to keep their sensitive data safe.