Looking For Unbiased Perimeter 81 Review. I’ve Got You Covered.
Traditional network security doesn’t work for today’s modern workforce.
With the rise of the mobile workforce and cloud transformation, the traditional network we once knew can no longer be trusted. Employees now work remotely from homes and in cafes worldwide, and companies are moving to cloud infrastructures such as AWS, Google Cloud, and Azure.
Given this, the traditional hardware-based VPNs and Firewalls we’ve relied on for over 30 years are no longer adequate in securing remote and on-premise access.
In a site-centric network, employees must be present on-site or use a VPN to connect with headquarters offices to access security services or the cloud environment. There is no segmentation or user awareness within the network. Cloud environments and SaaS services are not adequately protected and, in some cases, are being exposed to the internet, leading to massive data breaches.
One example of a vast data leak is the recent Capital One breach, which leaked nearly 106 million of the bank’s customers’ and applicants’ personal information.
Perimeter 81 Review: How Does It Help?
Perimeter 81 is a cloud-based VPN solution allowing businesses of all sizes to provide safe access to cloud environments, software, and on-premise services to on-site and remote employees. Two-factor authentication, split tunneling, permission management, and DNS filtering are among the features.
The tool, powered by the renowned SaferVPN, makes online protection easier, enabling employees to work safely while remotely accessing their work.
The service transforms the conventional corporate VPN experience by ensuring that it provides this power-packed approach regardless of what your employees are doing or from where they operate, using a next-generation advanced Cloud VPN solution and dependable hardware-free cybersecurity technologies.
This service is also ideal for multi-device users, especially those who switch devices frequently.
Why do you need a good VPN proxy?
Businesses have been using corporate Virtual Private Network (VPN) systems to give remote workers safe access to company intranet IT resources like SaaS applications and databases.
Conventional corporate VPNs, on the other hand, necessitate the deployment and operation of physical VPN servers, which are costly to install and operate and require a lot of technical competence to manage.
They’re also inflexible when considering having unified access to resources and material hosted on various networks, such as conventional private cloud storage, physical servers, mobile devices, and the Internet of Things (IoT). They fail to stay safe when faced with daunting technologies like the Bring Your Own Device (BYOD) trend (IoT).
Perimeter 81 Ease Of Use: My Opinion
What Features Do You Get With Perimeter 81?
More than just defense is covered by Perimeter 81. Business owners and IT security executives now have access to unrivaled network visibility.
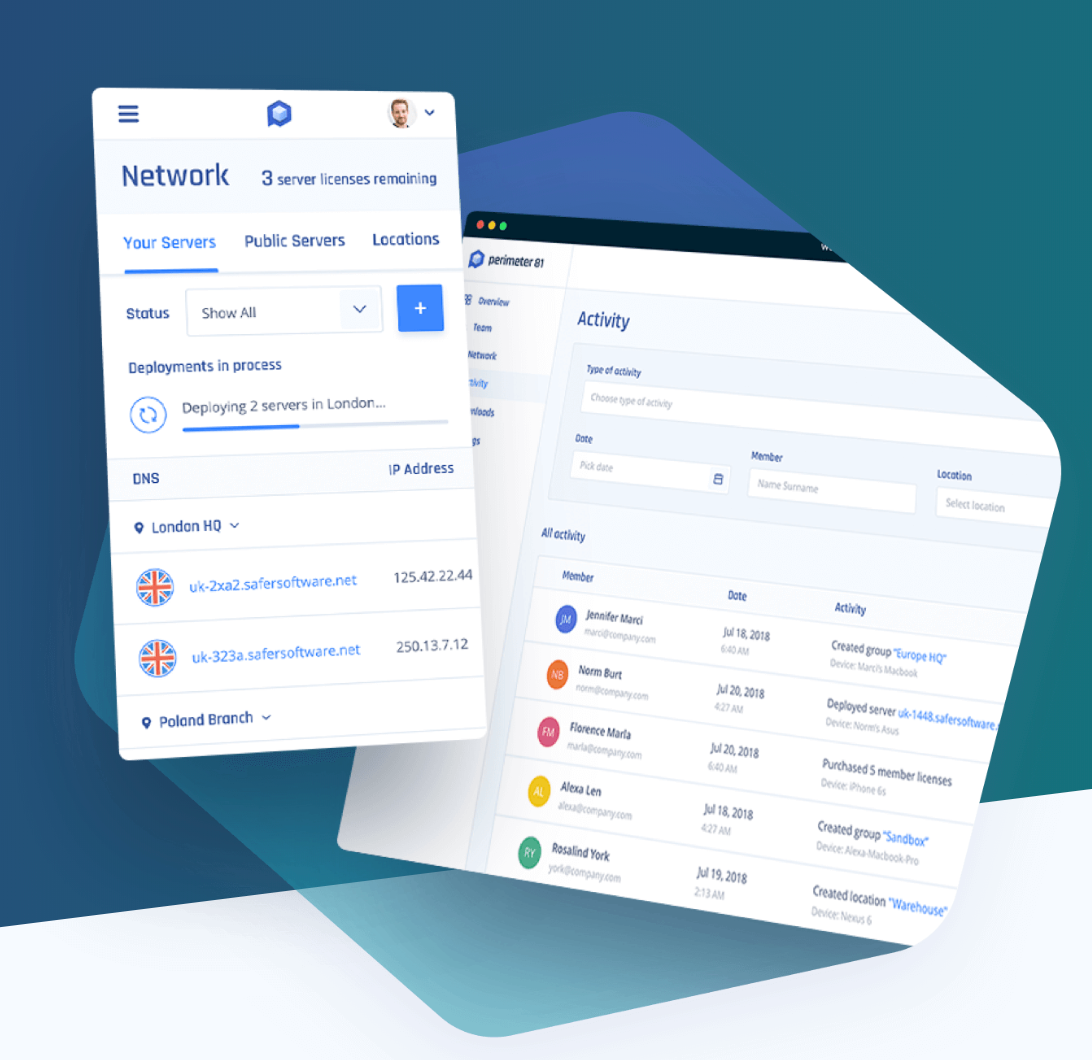
Since its flexible cloud management software provides a 360-degree view of your network security, you can spot any suspicious behavior immediately. This ensures you control your team’s and server’s settings and employee network and service access.
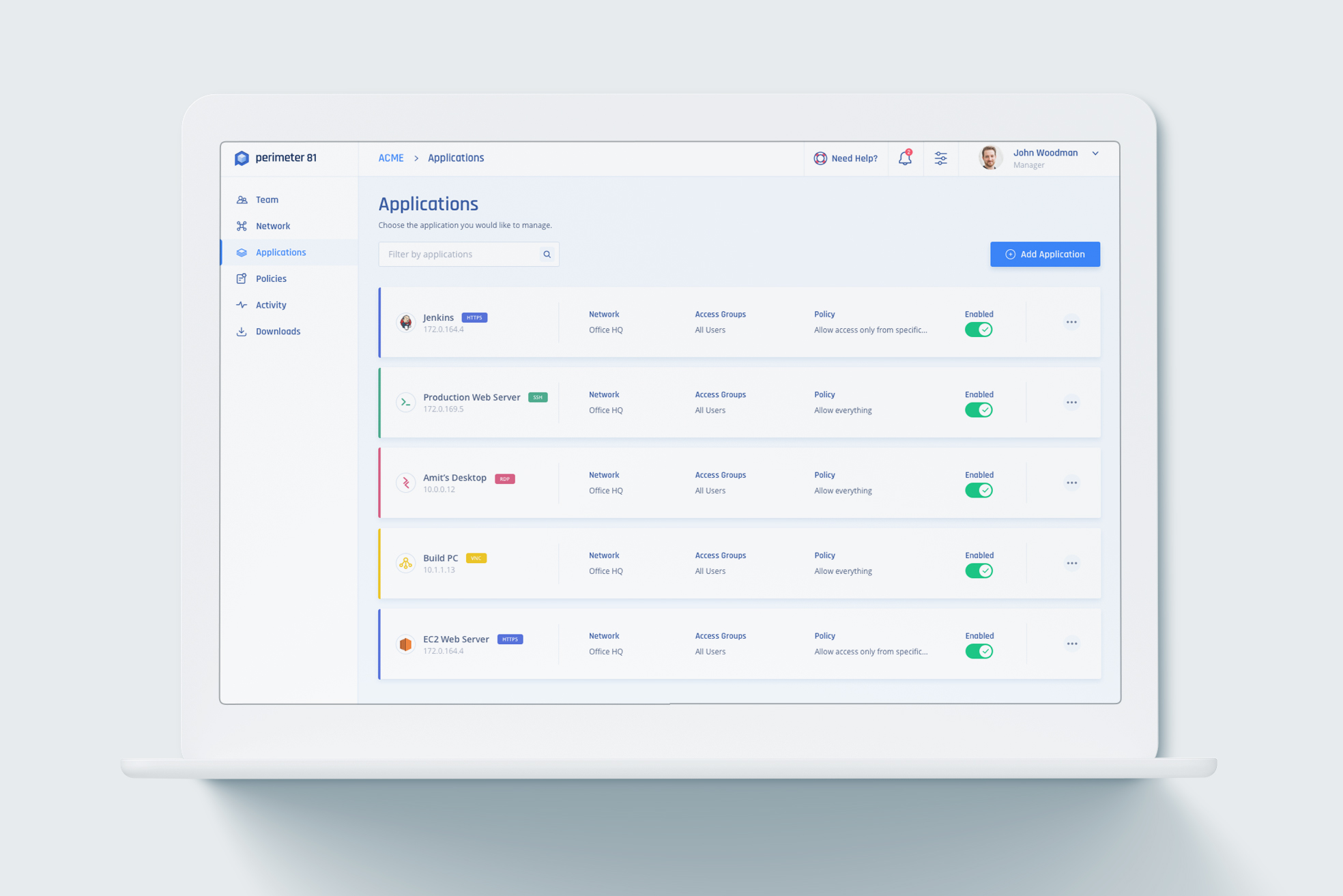
The platform offers all of the benefits of a conventional corporate VPN, such as safe remote access to company intranet resources and security while accessing the resources over unreliable public WiFi networks, without having to go for costly physical servers or the highly skilled staff needed to operate them. The following are some of the highlights:
HIPAA Healthcare Compliance
Perimeter 81 assists healthcare organizations in achieving HIPAA compliance by securing ePHi with end-to-end encryption and built-in two-factor authentication (two-factor authentication).
Data Protection for Finance
Perimeter 81 protects vital financial data from cyber-attacks for finance companies by protecting on-site and on-the-go access to confidential data and corporate resources while shielding them from the public Internet.
Multi-Tenant Cloud
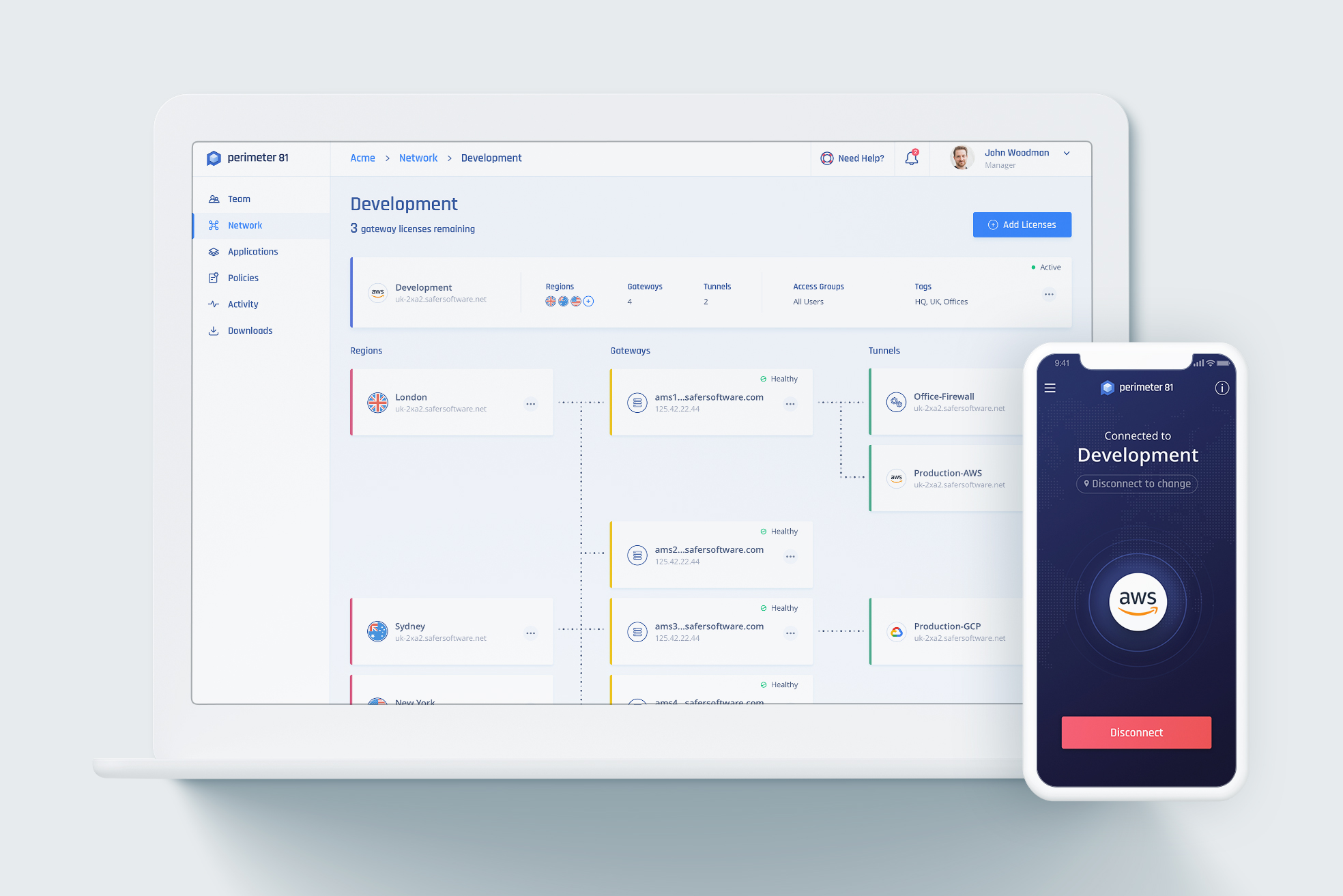
Perimeter 81 allows you to implement multiple networks through its user-friendly web portal, each with its own set of permissions. Using IP whitelisting, these networks can easily be linked to a central office, interconnected with each other, or connected to cloud services like Google Cloud, Amazon Web Services (AWS), Azure, and several SaaS services.
Single Sign-On Integration
Individuals or groups can handle access to company resources using the web interface, which integrates Active Directory, Okta, GSuite, and Azure AD.
Perimeter 81 also offers the following list of features and functions:
- Flexible access to non-traditional network services, such as Internet of Things (IoT) resources and cloud networks.
- The servers can be scaled dynamically by developing private VPN server gateways on the fly, with every gateway having a unique static IP address.
- Multiple user groups having team permissions can be handled from an intuitive and centralized management portal, allowing administrators to grant granular access permissions.
- Allows admins to keep track of network operations, such as bandwidth use, identify the resources accessed, and detect network issues and anomalies.
- Easy-to-use applications are available for macOS, Windows, Linux (including Linux X64), Android, and iOS. The majority of the apps offered have a kill button.
- Easily access a wide public VPN network that is available to users.
- When using unsecured or unknown WiFi networks, it provides automatic WiFi security.
- Allows two-factor authentication to be used for added protection.
- Improves user authentication by integrating with identity providers such as Google Suite, Microsoft Azure Active Directory, Okta, and OneLogin. Via your network’s Active Directory/LDAP Connector, Perimeter 81 also offers its native On-Premises Active Directory.
- Integration with Splunk. Allows businesses of any size to search, evaluate, and view data gathered from the IT infrastructure, giving you a complete insight into your Perimeter 81 operations.
- Support is available via live chat and phone 24 hours a day, 7 days a week
Advanced SMB-Friendly Cloud VPN
Perimeter 81 acknowledges the threats and difficulties faced by your company’s employees while relying on cloud-based technologies, as many fast-growing SMBs engage teams that operate on the go. Geo-restrictions, country-specific online censorship, and insecure Wi-Fi hotspots are all examples of this.
As a result, the VPN program encrypts all of your network traffic with single-click applications, automatic Wi-Fi authentication, and a cloud and team management portal, along with other features. The service has a single-click web management console for various devices, including Windows, Mac, Linux, Android, iOS, and Chromebooks.
Intuitive & easy to use
Perimeter 81 has been designed to be management-oriented and serves the purpose better than other VPN providers since it is specifically configured for business use.
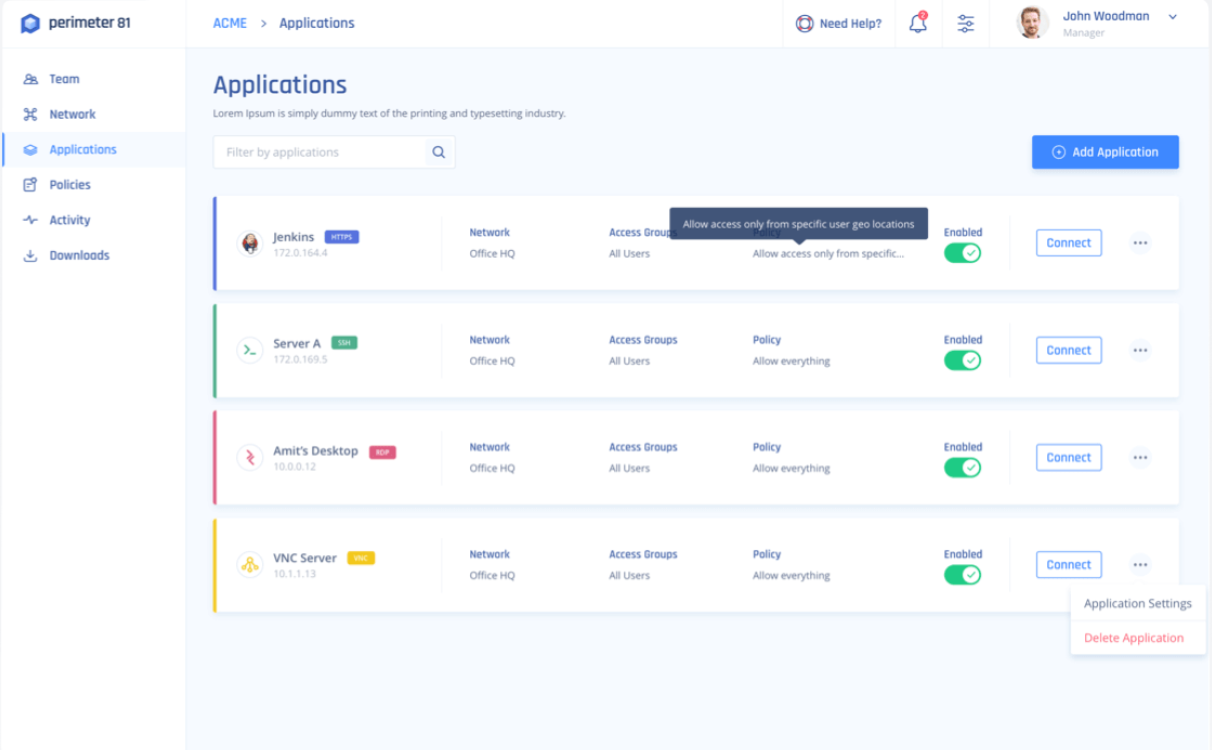
It’s very easy to set it up and get it ready for use. After you’ve created an account, you’ll notice that you get a very well-organized account page that offers a variety of management options, such as network view, team view, and activity view. You may build groups and assign them to unique server locations.
All you have to do now is invite your team members, install the applications, and build user groups to get started. The installation itself is a piece of cake. You can download the app on your favorite platform by visiting the link in the website’s Downloads section. Then, simply follow the wizard’s instructions to finish the installation of the app.
The app’s user interface is simple, intuitive, easy to use, and customizable. Working your way across the app’s functions is pretty smooth, and you don’t need any prior knowledge of IT. Simply click the appropriate icon next to the green Connect button for selecting the VPN location (organization or public), then click “Connect.”
When activated, the automatic WiFi protection options and kill switch and the ability to select different protocols improve network security.
In case you get stuck, Perimeter 81 has a comprehensive guides section on their website with various user manuals that give you step-by-step guidance on all aspects from how to correctly set up the VPN to the tiniest tweaks that can make your network function more smoothly.
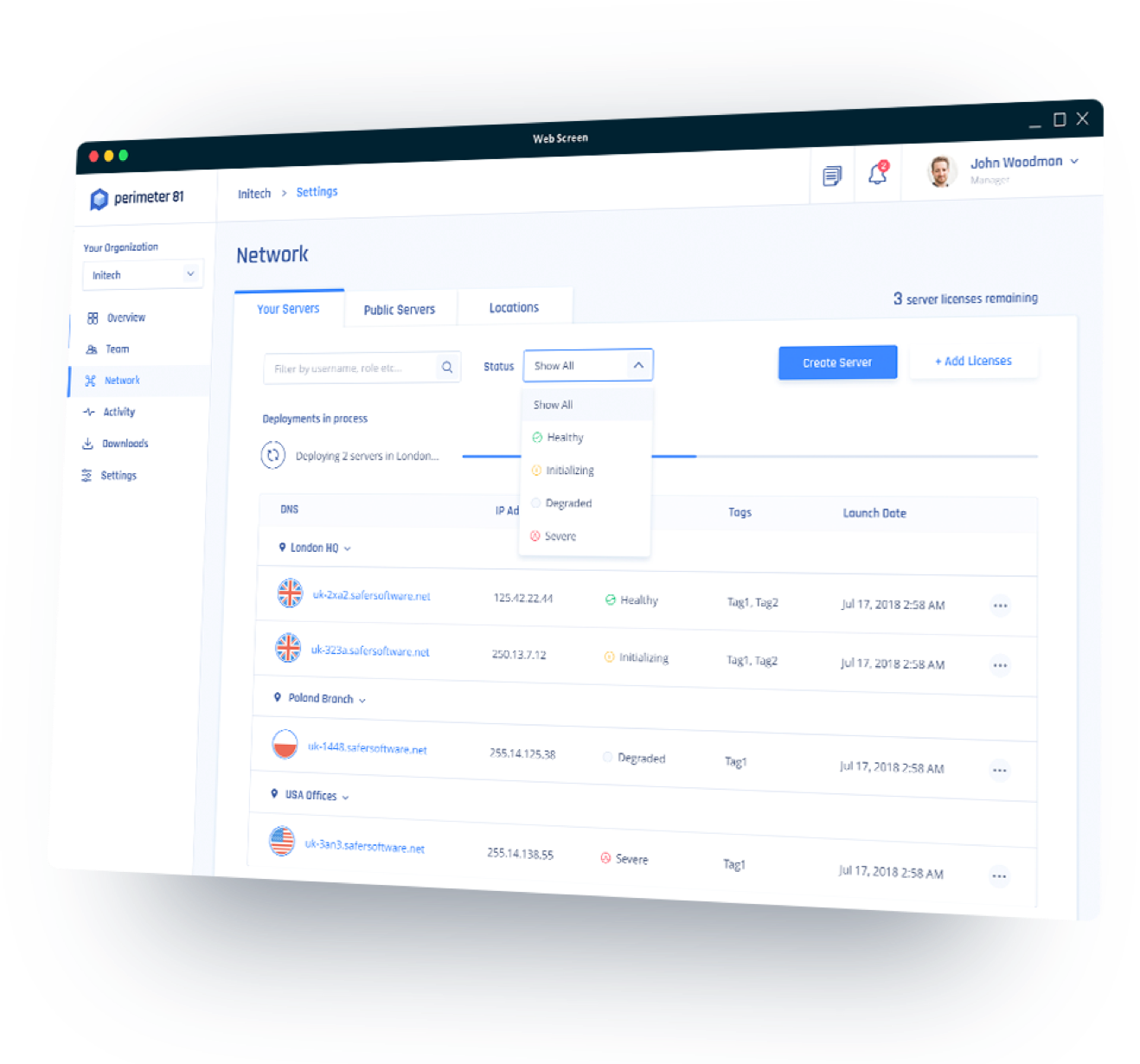
Create Multiple Secure Servers
Multiple servers may be set up at the same place or in different parts of the world. Private servers can be created in some US cities, including Toronto, Amsterdam, Singapore, Bangalore, London, Frankfurt, Paris, Sydney, Tokyo, and Israel.
Buying a fresh new license will only take a few minutes if you need another server. Alternatively, you can delete one server or build a new one with the same permission. It takes about ten minutes for a server to become operational after it has been developed.
Private servers usually serve as safe access points to corporate data. There are instructions for connecting to LAN resources using a firewall and personal cloud resources like Google Cloud Platform (GCP), Amazon Cloud Services (AWS), and Heroku Private Spaces.
Speed & Performance
At this time, we just have preliminary speed test data. Perimeter 81’s speeds aren’t bad, but they’re also not thrilling. With a weighted average score of 27.01 Mbit/s, the raw average / maximum burst speed results are 51.1 Mbit/s / 282.5 Mbit/s.
However, since results have been slowly improving over the last few days, they can still significantly enhance until plateauing. This article will be updated as needed.
Reliable Customer Support
Guides, white papers, images, webinars, and API documentation are all available via Perimeter 81’s extensive support center. Professional video tutorials and how-to guides cover installing the app, building custom networks, and managing community policies.
With Perimeter 81, it’s impossible to get lost. To begin with, self-help is a breeze because the official website is highly detailed and includes a thorough guides section. There, you will quickly find answers to the doubts and questions, along with troubleshooting instructions for various common technical problems.
All users can access a chat feature available 24 hours a day, 7 days a week. Additionally, anyone with a valid subscription plan can send a ticket to the team via email, but Enterprise and Premium users will receive a faster response than Essential users.
Don’t worry. Their response times are still reasonably quick; they replied within a couple of hours after we contacted them. They have also gone a few steps above and beyond by assisting us in selecting the most appropriate subscription.
With Perimeter 81, You Can Put An End To Ransomware Attacks:
The Meredith Respiratory and Sleep Centre is the largest sleep disorder clinic in Southern and Western Sydney, with four locations. They provide individualized sleep treatment and care, including various sleep exams, oxygen studies, wakefulness tests, expert guidance, and assistance.
Meredith was a hybrid workplace before Covid-19 arrived in Australia, with around a third of the workers working from home. Everyone could use the cloud-based Office 365 for email, but the on-premises electronic patient medical record system required a VPN and the Remote Desktop Protocol (RDP).
Because RDP came standard with Windows and was simple to set up, it seemed the ideal choice for accessing the corporate network. More crucially, non-techies who were required to enter an IP address and password found it simple. On the other hand, Hackers found RDP to be just as simple.
Ransomware has become a monthly occurrence.
We were getting hacked monthly because of the RDP,” claims Meredith Respiratory and Sleep Centres’ IT Manager, Omar Matter. “If a ransomware attack was detected, They have to shut down the network for an hour and restore our electronic records system from our offsite backups.” They only lost an hour or two of data on average.
However, if it was a severe attack and anyone didn’t notice it until it was too late, they may lose a full day’s worth of data.”
Omar was considering Perimeter 81, but a high-speed VPN wasn’t high on his list of priorities. When the company’s accounting system was hacked, everything changed overnight.
With zero trust, attacks drop to zero.
Omar started the accounting system from a backup and quickly applied for Perimeter 81’s Zero Trust access. After completing the basic setup in a few hours, Omar deployed Perimeter 81 on the remote users’ laptops.
“Ransomware attacks reduced to nil immediately after we converted, making life easier for users.” They found the desktop agent with Two-Factor Authentication to be highly user-friendly. What’s more, customers said their access to network resources at any of our offices was faster. Perimeter 81’s Site-to-Site Interconnectivity and Split Tunneling features are responsible for the improved performance.”
Perimeter 81 is a cloud-based solution that scales easily and allows you to make network modifications quickly. When COVID-19 hit Australia, for example, Meredith promptly relocated all its staff to remote work, putting the corporate network and applications in danger.
Perimeter 81 is now an essential aspect of their IT strategy. I don’t think Meredith could run a business without it in general. It’s also given the network a lot more flexibility. Their ransomware problem turned out to be a blessing in disguise. They would have been in a lot of trouble if we had gone through the COVID time without Perimeter 81.
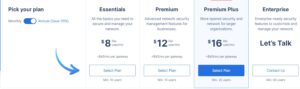
Perimeter 81 Pricing Plans:
Perimeter 81 Customer Reviews On Facebook:
FAQs On Perimeter 81 Review:
How is Perimeter 81 VPN different from normal VPN?
Perimeter 81 replaces the traditional business VPN experience with one-click deployment and unrestricted bandwidth. It allows you to connect private servers with dedicated IP addresses and delegate them to various teams, allowing each team access to unique resources. Perimeter 81 encrypts both inbound and outbound traffic to keep the company's assets and data secure from theft and hacking.
What functions does Perimeter 81 offer?
The tool offers powerful features like two-factor authentication, split tunneling, permission management, and DNS filtering, allowing online protection easier, enabling employees to work safely while remotely accessing their work. The service transforms the conventional corporate VPN experience by making sure that they provide this power-packed approach regardless of what your employees are doing or from where they operate, using a next-generation advanced Cloud VPN solution along with dependable hardware-free technologies for cybersecurity. This service is also ideal for multi-device users, especially those who switch devices frequently.
Is Perimeter 81’s DNS Filtering reliable?
Yes! Perimeter 81 offers advanced DNS filtering, which allows you to fine-tune what content gets filtered. You can also filter based on a number of predefined parameters and categories in addition to basic whitelisting and blacklisting of domains.
What does the Cloud Management Portal do?
The Cloud Management Portal helps you to control servers, permissions, as well as team members, is at the core of Perimeter 81. It also helps you to keep track of how your team is using the VPN software.
Is Perimeter 81 easy-to-use?
Perimeter 81 is very easy to use and has been designed to be management-oriented, and serves the purpose better than other VPN providers since it is specifically configured for business use. It's very easy to set it up and get it ready for use. After you've created an account, you'll notice that you get a very well-organized account page that offers a variety of management options, such as network view, team view, as well as activity view.
Do I get Wi-Fi security with Perimeter 81?
Yes! Perimeter 81 offers automatic Wi-Fi authentication and advanced setup to ensure that the employees are safe when they need to connect to these hotspots when working on the go.
Is Perimeter 81 suitable for small-sized businesses?
Yes, indeed! For small businesses, Perimeter 81 is the perfect VPN option. To learn more about the best features, read the post. They acknowledge the threats and difficulties faced by the employees of small-scale businesses while relying on cloud-based technologies. Their VPN program encrypts all of your network traffic with single-click applications, automatic Wi-Fi authentication, a cloud and team management portal, and other features. The service has a single-click web management console. It is available for a variety of devices including Windows, Mac, Linux, Android, iOS, and Chromebooks.
Which plan is suitable for large-scale businesses?
The premium plan is the best for large businesses because it provides advanced management network security features for larger businesses. The Premium plan is designed for groups of at least ten users who obtain priority email support. You can also go for the Enterprise plan, which is for companies with at least 50 employees, and email support and response are prioritized 24 hours a day, seven days a week.
Quick Links:
- Best Cheap Cloud VPS Hosting
- How To Make Money Online With A Reseller Hosting Business
- Cloudways Laravel Hosting Review: Should You Try It?
- CloudCart Review
Conclusion: Perimeter 81 Review 2024
If you’re a company that needs to constantly update your security tools and make sure they are aligned with the latest compliance requirements, then Perimeter 81 is for you. Perimeter 81 offers a SaaS solution that simplifies networking and enterprise-level security without any manual configuration or hours of setup time.
Get fully secure access to all of your most valuable resources from one cloud edge platform — it doesn’t get more convenient than this! And if you want ease of use combined with high levels of security, check out Perimeter 81 today!
It is very easy to schedule a demo with the Perimeter 81 team. Simply visit our Demo page, provide a few pieces of information and the Perimeter 81 team will provide you with a 1:1 customized demo, explaining how Perimeter 81’s solution can help to address your organization’s network and cloud security needs.
If you find this post helpful then kindly share it on various social media channels like Facebook, Twitter, and LinkedIn.





Well, my team was using a previous product by another company and it had become old. We were tired of not being able to see all the data in one platform without security problems so we switched over to Perimeter81. It works with our enterprise on-premise architecture smoothly and there are no gaps or holes for information to leaks out into other areas that could potentially end up outside the organization. The level of protection has been excellent for us because like I said this is something about which we care deeply as a boundary is always important when dealing with sensitive information.”
I found myself constantly having to defend my network when I started using Perimeter 81. But this cloud-based networking service, with its SASE platform and high standards of security, did all the heavy lifting for me! I had a total peace of mind and could focus on running the company while leaving my tech guru work mainly up to them. You’ll get spared from malicious attacks by hackers faraway in unknown corners of the internet so you can seamlessly provide your services around the world without worries.”
Perimeter 81 lacks a key feature that I forgot I used every day until it wasn’t there. I support multiple cloud-based businesses and have been introducing each of them to perimeter81 as a great easy to manage vpn with SAML SSO integration capabilities. It works flawlessly for all of my clients. But as an administrator that needs to switch between organizations regularly the client’s lack of support for multiple tenant profiles is a huge pain in my back side.
In addition to the lack of profiles, as of 2022-06-22, there is a bug where static routes are persisted between sessions on the client side, even if you log out and log into a new tenant. One client that requires a static route set up on the gateway causes me no end to headaches as I had to uninstall and reinstall the client to flush the route. Now I am running connections for that client inside a virtual machine until they have a modern multi profile client.
When designing an enterprise-grade cloud computing platform, it’s important to have the right balance of features. Perimeter 81 strike this balance by having some advanced protection tools that are designed to maintain your data privacy and prevent cyber attacks. For example, they employ FIPS 140-2 validated encryption for both technical and physical data security of critical infrastructure. They also make use of intrusion detection algorithms to protect against weak authentication protocols used in brute force attacks.
“This is the best company. They have this amazing product where they replace your firewall with an artificial intelligence that works in 45 different languages, encrypts everything you do, and has six levels of user authentication!”
The Perimeter 81 is an excellent platform that offers advanced security functions and a wide range of channels. In building the software, they adhere to the highest standards in compliance, which is great for organizations that worry about their data’s protection. I’ve been using it at my company for years and never had a single breach in network security. During installation, they will reach out to you with all the things you’ll need so there are no delays when it comes time to use them – everything from printable screenshots right through suggested best practices when setting up your Wi-Fi connection. If you have any questions or problems though do not hesitate to call!
I don’t know what I would do without the Perimeter 81! My data is super secure and it’s easy for me to stay connected.
When you run an enterprise business, keeping up with all the latest developments can be a huge task—especially when there are constantly new technologies emerging on the market every year. Quite frankly, no one has time for that!
This is the most advanced security system I’ve ever seen, and it was easy to install. Just a few clicks and my device was secured with Perimeter 81’s latest technology.
I work in IT, so you can assume I know my way around an edge. When I saw that Perimeter 81 SASE was the only network that offers SIEM integration, it immediately became my top choice. Not because I’m an engineer who’s always looking for new things to build, but because I’m sick and tired of hearing rundowns about breaches at every staff meeting! With Perimeter 81, your data is encrypted before transmission (specifically AES-256), your node won’t be flooded with DDoS attacks if someone tampers with their DNS settings; it’s got everything you need for secure networking right on one platform!
I’ve never been this excited about software in my life. Perimeter 81 is easily the most innovative new cloud-based networking solution on the market! We were seeking a next-generation approach to edge security, and found one here.
This cutting-edge software provides brilliant data management without sacrificing efficiency or productivity. I can gladly say that my search for better technoloy has finally stopped Thanks to Perimeter 81!
I used to work for a major company, but I had my most creative ideas while waiting in line for lunch. My supervisor was so impressed with the idea they made me come back to work on Monday just to show her my thoughts. When she goes into detail about how it would help our old machinery and redistribute research that’s been out-of-date, I could see her eyes light up right though my coworkers have told me were lifeless years ago. A light still burns there – one that reminds me of the days when projects weren’t weighed down by budget cuts nor halted by politics or bankruptcy – but fueled by innovation. That’s why I’m now convinced Perimeter 81 SASE is something worth checking.
Perimeter 81 is the latest and most innovative technological platform available on the market. I, for one, am so glad that my company bought it for our business! With its network security and reliable software capabilities, we can rest easy with Perimeter 81 protecting all of our data and information. They also really know how to keep things tight: you won’t find anything getting past them with their layered approach to securing your data with an unbreakable firewall. For those who need more convincing, just remember that this system is fully compliant with industry standards such as CISP compliance. As a user experience professional myself, I can’t recommend Perimeter 81 enough!
With Perimeter 81 SASE platform, your business will see an increase in productivity while ensuring that has the safest routes to data.
“It’s like Facebook, but you can actually control it.”
The team at Perimeter 81 really put in the time, so I wanted to give them credit for their hard work. You can’t get this level of cybersecurity anywhere else, folks!
“The best perimeter security you can get. The Perimeter 81 SASE platform offers a wide range of capabilities that your organization needs to enforce their IT policies. It is the only solution on the market that provides end-to-end encryption for both data and communications, ensuring private conversations and files stay confidential.”
My experience with this product is great. I’m a CIO and the IT department has been after me to upgrade our equipment for months, but I couldn’t find any information on new gadgets that would make it worth my time or money–until now! With the Perimeter 81 SASE platform, we were able to focus on building rather than maintaining what we already had. The best part about this product is that even though there are technical terms everywhere, the interface is easy enough for non-IT people like you and me to navigate without stress or difficulty. GE took feedback from CIOs like us into consideration by consolidating all of our networks using this one platform; it also cut down on our integrations time which made
I can’t express how easy it is to use this product. Set up was a breeze and I’m no tech genius! I know you want the full details on security, but let’s face it: most of us don’t really care about that stuff. You just need to buy something reliable with good customer service, and Perimeter 81 is totally the way to go!
I always have to worry about my company security. It really makes me laugh when I go blog shopping on Amazon and I can’t order anything because Amazon won’t ship it to the UK – they know how precious your data is! Well, luckily my friends at Perimeter 81 have it all sorted. They provide you with maximum security in mind, so if anyone ever wants to get their hands on your team’s records then good luck!
I have been doing IT work for a nonprofit organization, and I had some major security issues with VPN service providers. My company has been using Perimeter 81 as the only software on its cloud edge so all data is protected from outside threats. Because of this, we need to be able to access our resources anytime anywhere – no matter what Wi-Fi connection we’re working with!
I’ve seen the future and it is great! I read all about this new technology that can store data very securely. Thanks to Perimeter 81, private information never feels like it’s vulnerable again. Whether you’re storing secrets or browsing online, any website becomes our own private experience. The guy below me seems mighty impressed, so if he likes something your thinking of not liking well…
Natively-cloud managed security services save managers from more burden. Admins have to worry about the one server, the one firewall, and maybe a load baring switch. Laptops and mobile devices need their own software management solutions on top of that? I’m exhausted just thinking about it! And then came Perimeter 81’s offerings – a pittance for all of those headaches still costing me for legacy hardware, or worse – an abominable home brew solution! Plus you get alerts if something new pops up right away instead of waiting for some automated scan to show you what you already know from before!
I’ve always wanted to live in a house with gates, but it can be beyond my means. Trying to do all that work myself? Forget about it! Plus the yard space is too small for that kind of thing. I checked around and nobody beats Perimeter 81 when it comes to their network protection service (SASE). Security like none other, plus they keep you up-to-date with anything important in your area. What more could anybody ask for in an access platform?
The perimeters have been breached. Doesn’t it feel like you’re always replicating or reconfiguring solutions that do very little to protect your data? It’s time for a change, but is the perimeter what needs protection? Historically perimeter-based security was enough – but now more than ever, an app is just as likely to be the point of entry. That’s precisely why Perimeter 81 offers one platform with powerful networking and security in an easily navigable cloud environment – no large hardware with many configurations needed either. Gone are the days when everything had its own overpriced hardware solution!
I use it at work, and I love the fact that there is no compatibility issues with other hardware like scanners etc. It also has filters in case my company’s bandwidth becomes limited/overloaded. Definitely worth shelling out for!
I had never seen anything like it before, and now I can’t live without Perimeter 81. I am super impressed by how comprehensive the platform is. It’s simple to set up and use under any circumstance. And best of all their prices are great too!
I’ve been using Perimeter 81 for the last year and I’m in love with it. When I first started out, all my alerts were driving me insane. It felt like every time I looked at my screen there was a new warning telling me one of my devices wasn’t configured correctly. I would read through them but not take any action because they were too much to handle on top of everything else that had to be done—I played musical chairs when it came to fires in the kitchen, turning up the thermostat in the server room since the AC went out, making sure nobody walked off with an Xbox controller… well you get it! The point is that switching over to this product has changed everything for me!
In the past I had to have two separate firewalls for secure and secure wireless. But now, thanks to Perimeter 81, my business has it all with a single cloud-based solution that’s easy to use. With a single interface, we can manage user access privileges and be protected from threats everywhere they go without sacrificing performance.
Traffic heading to your business will always be one of the most important issues you have to deal with. With Perimeter 81, you can rest assured that any data coming into or out of your company is safe and secure on our end. You can stop worrying about information getting intercepted on public Wi-Fi networks or wondering if your firewall is working properly ― with this service, all networking needs are resolved in an easy-to-manage package.
I never thought my organization’s data would be at risk. I heard about the reports on breached emails and credit card numbers, but couldn’t imagine that it could happen to me. That all changed when we switched to Perimeter 81 SASE platform earlier this year—protecting our information is now a no-brainer. In the past, we had security tools scattered everywhere—purchased from different contractors or cobbled together ourselves from free sources on the internet. So frustrating! Now it’s just three quick steps: Click a button in our dashboard of insights and enjoy knowing everything is safe with Perimeter 81 SASE platform’s latest encryption innovations.
When your team is on the go and needs secure access anywhere, we’ve got you covered. Switching to Perimeter 81 couldn’t be easier – they do all of the work so you don’t have to worry about it. My favorite part? All of our data is safe from hackers since I am using a VPN that encrypts every connection.
I was hesitant to try Perimeter 81 at first, but it really is worth the switch. I love how simple and easy their new system makes everything: no more clunky software for me!
That’s right! You heard it here first. Perimeter 81 delivers the highest level of networking and security in one cloud edge to help keep your organization up-to-date with ever changing security standards. The time is now!
“I absolutely love the new SASE, it has made my work so much easier. I can’t believe that one system does everything for me.”
Today is the day I say goodbye to legacy networking hardware. With the massive amount of data breaches, malware attacks, and rampant spyware, it’s no wonder why major enterprises are turning to cloud-based solutions at an unprecedented rate.
Perimeter 81 SASE platform outdoes any onsite, point security devices because by creating countrywide defenses in collaboration with leading firewall providers like Palo Alto Networks . Plus – Perimeter 81’s response to challenging cyber threats across all industries more than doubles that of other networks’ infrastructure. Durable for over a decade ago–and smart enough during your next meeting? You’ve come to square one by trying our foolproof network security solution today!
Perimeter 81 is a great product. It combines our enterprise edge security, with the ability to monitor your network from anywhere in the globe. Its intuitive dashboard makes configuration and management of both wired and wireless networks easy as can be. There’s also integrated endpoint protection for endpoints like laptops, workstations, game consoles or tablets.
I’ve heard stories of this company halting production of other products because they think their product is so good. They must be right- it worked perfectly for me! I was really surprised to see that the only thing you need to do is install one base module, which makes setting up and tearing down portions very easy. All the pieces were at my doorstep in just a couple days even though I live on the opposite side of the country from them!
Perimeter 81 is the only edge security solution that does it all! And do it quite well too. The software doesn’t even require any tinkering in order to protect your data. I used to cringe when I had to take care of an individual gateway, but now my life’s so much easier since I can just use this system for everything. It’s easy enough for an amateur like me to manage and saves time big time by not having to go through round after round of updates or setting things up over and over again on different devices every day. The interface is self explanatory and you don’t need people with technical skills at all, which means that anyone in the company could handle their own company’s needs.
“I highly recommend if you are looking for a security platform. Perimeter 81 is the best out there with outstanding reputation and product quality.”
The product image on their main site is deceiving because really, the whole SASE platform of theirs comes with one server. So had I known there was only one server included in Perimeter 81 Professional Edition (which on its own retails for $26000), I never would have bought it since there were cheaper buying options at first glance. Also they only offer 24/7 support.
I don’t know who these other people are that gave this thing low marks, but I am LOVING this product. Easy to install and run, the interface is customizable like any database would be (so you can change it to your tastes) and it allows me access to my company data from anywhere which has led significantly higher productivity!
I am not a security expert by any means but I have been using Perimeter 81 for over two years now. It has made my life so much easier that there are days where I just shake my head in disbelief that something like this existed. Other than the amazing features of the software, the customer service is always there when you need them no matter what time it is….and even if they can’t fix your problem online, you can reach one of their operators in less than five minutes which feels like next to nothing!
I work in IT, managing all of our networks for one of the largest companies in the world. I recommend Perimeter 81 to anyone that’s looking for a way to strengthen security on their company networks. With this software, we can control everything from logins and passwords to user permissions and even files on connected computers without having each employee install specialized apps like Symantec or McAfee. Not only does it make updates easy; we’ve found some other options aren’t secure enough for some of our data because they store data locally instead of remotely like we do with Perimeter 81 – A+ product!
I was looking for a safe, secured cloud product that isn’t too easy to hack into. That’s when I stumbled on Perimeter 81. Security-wise it has everything you could ever want; encryption keys, throttling, machine learning algorithms—you name it. And the best part is that if your data gets stolen or hacked by someone like me who knows their way around security systems (lol), this baby will take care of them in no time anyways.
Maybe you don’t think you’re all that into digital perimeter security. You might even be one of those people who believes that the security is just as important on the inside than it is on the outside, and with most products there doesn’t seem to be any real need for working so hard with your data-or maybe not so much your data but more your privacy. Still I’m telling you now after using this product…your appreciation needs changing.
After my company invested in another terrible platform and had to shift all of our content because of vulnerabilities that were surfacing after new software updates? I knew we needed something more secure than what we already had. We looked high and low and bought perimeter 81, great investment by far.
Before deciding to use Perimeter 81, we evaluated many VPN providers and I must say that I am very satisfied with the choice we made. Perimeter 81 not only makes network monitoring and management easy, it also enables us to achieve zero trust security through built-in SSO and 2FA integration. While we don’t need as much support for our previous VPN providers as we did in the past, when we do, the Perimeter 81 team can respond quickly and always be reliable. After using the Perimeter 81 solution, it is a relief to know that our employees’ connections are secure and solid. I would definitely recommend this service to other IT
I predicted great things for Perimeter 81. Their software is almost perfect, and my service has never encountered problems. The software-defined boundary is the future, and this company will go a long way.
With Covid, Perimeter 81 provides a solution that allows us to ensure that our employees can work safely outside of the office. In addition, we now have a single interface to manage our different offices. When we encounter some issues, the support team will quickly respond and resolve our issues.
With Perimeter 81, we no longer have to worry about managing our own VPN server. Using one-click deployment, we can easily add private servers and assign them to different teams, ensuring that only certain teams can access specific resources.
Perimeter 81 is a nightmare; you can never get through to anyone! Their sales team lies to you in order to persuade you to buy! They hooked me on the idea of helping me with my network, but they had to leave halfway through the setup since there was another meeting. They will not assist you in setting up a new computer. I’ve been waiting for support for my 1:30 meeting, and it’s now 1:52 and I’m still waiting.
Onboarding and implementation went very smoothly. I’ve been a client for about a year, and it’s truly helped my team access all of our resources during these days of remote working. The Perimeter 81 support crew is very approachable, which is a significant benefit.
Perimeter 81 is quick to respond and will gladly jump on a call to assist you, but that’s where the help stops. If you have a problem, they want you to uninstall and reinstall their client first. They’d rather blame your network/system than look into their problems.
During the outbreak, Perimeter 81 was quite helpful to our firm. We required easy and secure remote access for our WFH staff all around the country. I barely have to deal with a few settings because the setup was done for me. This was a lot easier than trying to set up and operate a VPN on my own. This is a crucial tool for remote companies, and I recommend it to other companies that want to become completely remote.
I have to use Perimeter 81 for work; once connected, it appears to be quick, but it crashes so frequently that it’s a nightmare to use. Actually, Ubuntu performs better than MacOS, but even so, uninstalling and reinstalling is a common occurrence.
During the epidemic, Perimeter 81 has made the move to a remote work environment a smooth one. For our WFH staff in the US, LATAM, and EMEA, we needed convenient and secure remote access. This was a lot easier than trying to set up and operate a VPN on my own. This is a must-have tool for any remote firm, and I recommend it to any companies looking to go completely remote. Their roadmap of new features will keep them competitive against market heavyweights such as ZScaler, Palo Alto Networks, and Cisco.
Until we switched to Perimeter 81, we were having trouble moving our AWS infrastructure. We were able to migrate our complete organisation (over 400 people) to the cloud without incurring the costly headaches and hours of manual configuration. Installing the agent is all that’s required.
Perimeter 81 has been quite helpful in terms of managing and establishing policies for our remote staff. It was thus much easier for me to communicate the concept of “zero trust” to my manager since he could see it in action. It’s quite simple to set up, and their support instructions are extremely helpful.
Control and manage security warnings while exploring our network and safely sharing data. Perimeter 81 is a fantastic platform for managing and controlling internet security, including tools and analytics for receiving data and alarms.
Perimeter 81 is a simple piece of software to use. It can connect to several servers all around the world. Users of Windows, OSX, and Linux can utilise the client. The web management is excellent. The only criticism I have of Perimeter 81 is that it does not yet enable Google authentication. Manual setting is not required for Linux users who do not have a native client.
With Perimeter 81, I like that I can communicate with my distant staff and that there are no bandwidth constraints. The pricing is reasonable, and customer care is available 24 hours a day, seven days a week. I didn’t care for the fact that it presently only serves Windows, OSX, and Linus users. My clients get their information from a variety of places.
Perimeter 81 is a cloud VPN that is simple to set up and use, with intuitive software and outstanding customer service. I was able to simply configure clients on macOS, Windows, and Ubuntu, and their great support team assisted us in connecting our AWS VPC to the VPN.
We moved away from Perimeter 81 because it lacked several characteristics, although they were on the road map when we spoke with them. I believe the product has a lot of room to develop and flourish. It’s simple to use and has several excellent features. It’s simple to use.
Run a team of 25 salespeople with laptops who connect from a hotel or coffee shop all around the world. There were a lot of hassles in the past with clients, updates, and so on. Now there’s nothing. Perimeter 81 allows me to protect my team without causing any headaches.
I can quickly and easily handle the onboarding and offboarding of external users and providers with the help of Perimeter 81. I can also design WebApps to make it easier for users and even IT managers to access information.
Perimeter 81 is a Cloud service that simplifies management and maintenance tasks, freeing the end user from the need for expensive hardware or complicated software. It works well with a variety of identity management systems. It also has several features that strengthen the security of customers’ endpoints, unlike other VPN solutions.
There’s so much I want to say about Perimeter 81. Utilizing this service has changed the way I work. But what really sets it apart is how simple and easy it is to use, even for beginners who need tech support very occasionally like myself. The ability to do just about everything with a single cloud application makes things so streamlined and convenient that I’m more productive than ever before.
Perimeter 81 has everything you need to keep your information secure and work easily from anywhere without having to worry about outdated hardware. Setting up Perimeter 81 is easy, and it provides top-of-the-line service at a low cost compared to competitors like Cisco or Symantec. The platform can be used offline in case of emergencies, which peace of mind knowing that our data will always be protected even if an emergency strikes! I give 5 stars out 5!
The Perimeter 81 is a major breakthrough in computer security for remote workforce. Forget the hassle of fiddling with traditional hardware! The platform not only offers absolute protection against prying eyes, but it also boosting productivity by reducing alert fatigue. Reach session transition time more quickly and forget complicated web-based systems with this lauded solution that will simplify your work day so you can finally focus on what matters.
I’ve used other security products, but Perimeter 81 is by far the best. I used to be paranoid of losing sleep due to device alerts all the time, and while some people may not agree with me on this one, it can happen that these alerts are even more a problem than the issue they’re alerting about! With Perimeter 81 you don’t have to worry about any devices running out of batteries at an inopportune time or needing constant updates–its automated. No need for manual updates or having old protocol software could get your organization’s data in jeopardy. In fact my security team was very impressed wit how well equipped it is against cyber threats like malware and ransomware.
I had been searching for a solution to create work access without having to drive everywhere. Perimeter 81 creates ease of mind knowing I can go about my day, with peace of mind that the sensitive data entrusted to me is safe and secure. This turned out to be the perfect fit! Cloud-based and user controlled, all from my laptop or phone so no matter where I am in our sales territory, I can securely connect with resources back home.
The IT Department at my company was a mess. All kinds of things would happen, from service outages to data breaches. I liked the idea that they were moving everything to one system with an edge server (so it can’t be hacked) and the software is all on there – so you don’t have to install anything. It’s not perfect, but since we’ve installed Perimeter 81 SASE access security thingy, life in IT has been much better!
I was so tired of dealing with passwords and having to remember that I have a 99 character password limit. As soon as I came across Perimeter 81, I made the switch immediately! It’s been much easier this way. Reports don’t give me any trouble anymore, and my coworkers can access our work files anytime from anywhere without me needing to unlock the door myself every time they want to come in. If anything goes wrong—a router goes out or whatever—I just call their support line and even they can remotely log into my PC with no problems at all!
With Perimeter 81, I can securely access my company’s data anywhere I need to be. Now that our employee base has grown, we needed a server that could handle the new demands. The IT department was an unending bottleneck of requests and complaints. With Perimeter 81 SASE platform, all those problems went away with just one click on the app! So many programs are in use at once when managing remote employees so it’s important for companies to find a way to stay secure while being flexible enough for out-of-office workers to get their work done remotely as if they were still in the office. That is where Perimeter 81 walks its talk!
Perimeter 81 is like Uber meets CISCO VPN but better
As a remote worker, I thought my days were numbered. An all-in-one solution for dynamic access to our network from any device that we may want to use on the go? Sign up for Perimeter 81! Our IT department loves it too since with one user interface and many features, it’s less work for them so they’re not having as hard of a time coping.
I have never been the head of IT for a major company before, but between all the sprawl and complexity with other security products and where they stand in this constantly changing landscape, I honestly don’t know how these people are getting anything done. With Perimeter 81 my team can actually provide our engineers what they need to keep them safe from outside threats! This makes my life so much easier- if you ever want to join your team on a video call and not worry about checking twenty different firewalls just be sure you see their reaction when we tell them that everything is set up based off one simple login ID. Easiest thing I’ve done since taking over this role!
Although I hesitated at first, this is the absolute best solution when it comes to remote access. As the IT department for my company, I found a variety of ways that employees were performing outside tasks like data transfer and emailing with their personal devices. Perimeter 81 helps us keep everything synced up from whatever device we’re working on. Plus they offer 24/7 support if any issues arise and you can cancel your subscription whenever you need to!
I was apprehensive about switching to this new service, but quickly I realized what a great decision it had been. The Perimeter 81 SASE platform delivered much higher performance than the previous security system. You can rest assured that your data is protected thanks to their highest standards of software security compliance and SAGE operates within government-grade data centers. It’s no wonder that Fortune 500 organizations are jumping on board with this leading edge technology!
I dig the new Perimeter 81. My old firewall was wearing thin, weighed me down, and gave me no protection at all. Sure, some vendors offer more security than others but it’s hard to know which one is safe if you want stay out of jail and guard your data only for yourself!
This time I did my homework. I kept an eye on what my friends were up to at work, looked into their network perimeter vulnerability projects, and saw how seriously they take their job nowadays with a whole new generation of “edgy” servers that are easy to scale anywhere in the world. The secret lies in their networking ability: With support 4G-LTE/3/2 networks including 3G WH
I would 100% recommend Perimeter 81 SASE clients to anyone who is looking for an easy and quick way to securely access company resources from a remote location. I’m actually super stoked about being able to work remotely, because it means my commute time has been cut in half. Plus, the application works on any device! It’s so cool.
I switched from my old security service provider at the advice of my IT administrator and it’s been sooo easy. I never used to log out, but this system encourages you to do so because you can’t use your account offline; that really helped me stay on top of things. It’s nice knowing that they’ll inform me if any issues come up with the network or anything, because there haven’t really been too many. If anyone from IT is reading this, THANK YOU for switching providers for us!!!
We had some big security needs and couldn’t afford to build out all of the hardware, so we got Perimeter 81. We don’t need to worry about pesky legacy equipment after moving over to this platform which saves us a ton of time too! The flexibility is great too – I can do more on my break because I don’t have access issues like before.
Perimeter 81 has made my job so much easier. I can finally connect on a regular basis with other remote team members and share ideas without any worry about security. That means we’ve not only been able to collaborate better, but our productivity has increased as well! It really helped that the system was easy to set up and use- no complicated configurations or long instruction manuals needed here!
Perimeter 81 is the future of remote secure access and provides an excellent experience for my team on their iPad. My laptop had security issues, and my business applications keep getting hit with viruses while I’m traveling. There was nothing to do until I heard about Perimeter 81’s solution which uses end-point encryption at the VPN gateway to protect networks because it never connects directly with unsecured Wi-Fi networks or public hotspots. It also encrypts data in transit so your information is safe – unlike other internet based solutions that open up your security to hackers roaming free on the open web. That smart design means improved performance! In testing mode, speeds were even 20% better than anything we’ve experienced before – no interruptions in HD video streaming
The fact that Perimeter 81 has solved security tool sprawl and alleviated alert fatigue is a huge relieving idea. I don’t know about you, but all the hoops I need to jump through if an individual rejects my multi-factor authentication can be quite annoying. This platform from Perimeter 81 takes care of AIDEA as well … it’s brilliant!
I don’t know what I would have done if Perimeter 81 hadn’t existed. I’ve been traveling extensively for work lately, and with the current global climate of security risk, it’s hard to feel safe at home. Not only is my job dependent on remote access or meeting in person with clients but also not being able to trust a hotel staff when you leave your belongings unattended ever again? The idea alone makes me cringe! But luckily I found this cool little service called Perimeter 81 that actually encrypts all of my data so no one can still see my *ahem* favorite photos while abroad (or anywhere, now).
One of the best things that I tried out in a long time. Moving from wired to wireless access points was seamless, and my employees on the go have not even noticed any changes other than an uptick in bandwidth for their devices. You can’t just sign up and hope for the best – you need somebody to ensure your network is secure before it’s too late, but Perimeter 81 service does that better than anything else we’ve seen so far.
Perimeter 81 has quickly become my favorite new thing. I did the research and it was amazing that they provide a free consultation to help me understand what package best suits my needs. And all at this reasonable price? It doesn’t get better than this! Awesome Perimeter 81 review, Loved It!
I never knew how much I needed this until I had it. Perimeter 81 saved me from a world without home workshops!
The IT department has redefined the way we secure networks and monitor data access while unleashing our workforce. With Perimeter 81, I can sign on from home in a matter of minutes and complete my tasks without worrying about having to bring a high-end laptop out with me all the time. Plus, when it comes to updates in cybersecurity or any new threats that arise, my staff is always notified immediately so that we can stay connected and streamlined.
Perimeter 81 SASE platform is great for small businesses with at least 10 branch locations because it’s an affordable way to keep up with the latest security standards. The web interface may seem a little cumbersome, but I was surprised at how easy it was once the company set their own templates. It’s worth spending some time training your IT team on how to get the most out of every feature, but they are all pretty intuitive- you don’t need more than 15 minutes of training before employees are operational without direct oversight from higher ups.
This product has totally changed my life. I can do everything I ever wanted without burning through data like it’s nothing. Not only that, but Perimeter 81 gives me high-level networking and security in one cloud platform so I never have to worry about anything happening to our data as long as we’re using this awesome service.
I never wanted to write a product review, but business demands and the economy made me no choice. Perimeter 81 saved my IT company from bankruptcy—quite literally! Frustration had finally reached its peak and I was ready to throw in the towel when I came across this service that gave our firm a fighting chance. You won’t find any legacy hardware or complicated layers of security. What you will find is peace of mind knowing your remote workforce can be as productive as they would be on-site at headquarters without putting data at risk in the process.
Security for the remote workforce has never been more important than before. With devices like printers, scanners and work stations being shared amongst a large number of employees, keeping up with security on company documents is hard – but Perimeter 81 makes it simple! It is easy to forget the old scanning equipment from years past after experiencing this way of working. The best part about using this platform is that you can stay secure as a whole without having to worry about individual documents going unprotected. This amazing software ensures your data remains safe by adhering to some of the most high standards in cybersecurity compliance. Rest assured that your organization’s data remains secured when you start using Perimeter 81 today!
“I tried over fifty SaaS solutions and the one that worked best for my team was Perimeter 81. The app is completely efficient, with many helpful features.”
I have been in the field and disconnected from most of my team for weeks at a time. Yikes, this is no fun! Having 15 different passwords between all of my applications was getting to be really frustrating. Thank god I found Perimeter 81’s SASE platform. It securely logs me into every internal system back at HQ via one global identity that never leaves my device unless I choose to share it for business purposes with someone else like yah girl Michelle, who can do some work on her laptop while sitting next to mine during brainstorming sessions on our company retreat out west last week so we could take advantage of special deals offered by the hotel staff only because she had exceptional negotiation skills. Win-win situation since nobody likes jet lag
This is the future of cloud computing. From security to privacy, Perimeter 81 was built for an age that puts your data’s safety at its core. They never store copies on their servers and every single action you take with your data is encrypted end-to-end.
Perimeter 81 is the best security I’ve used, and they have a warranty for up to 3 years. The software has been easy to install and use so far, since it goes as fast as my old anti-virus program. It took me less than 5 minutes to set up on my home laptop. With their user-friendliness, generous free trial period, and high ratings from Windows Central readers like myself with no connection problems that might co-opt your sensitive data—I’m really happy that I decided on Perimeter 81 after a lot of research!
The Perimeter 81 Security Active Edge is the most secure edge solution on the market. With consistent monitoring and updates, you know that your data is safe and protected because it’s backed up by a security team who lives to protect your device. Plus, get easy access for on-the-go work with remote connectivity iOS or Android!
“You know what’s hard? It’s hard to pinpoint a vendor who could really help us with our network security. Perimeter 81 have been great! We’ve been able to consolidate so much of our data thanks to their software.”